IA para la Detección de Anomalías en la Ciberseguridad de la Cadena de Suministro
Una Necesidad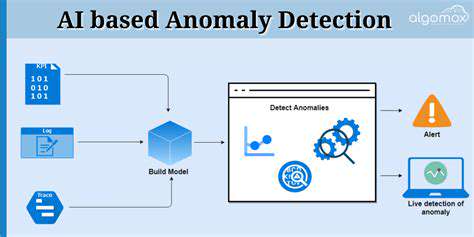

La naturaleza globalizada de las cadenas de suministro modernas crea intrincadas redes de procesos interconectados, haciéndolos vulnerables a una multitud de posibles interrupciones. Desde eventos climáticos inesperados que afectan al transporte hasta la inestabilidad geopolítica que afecta al abastecimiento de materias primas, la posibilidad de que se produzcan eventos imprevistos pueda afectar a...
Detección de Anomalías Impulsada por IA: Un Cambio de Paradigma

Detección de Anomalías Impulsada por IA: Una Herramienta Potente
La detección de anomalías impulsada por IA es un campo en rápido crecimiento con implicaciones significativas
Más allá de la Detección: Implementando Estrategias de Respuesta Efectivas

Más Allá de lo Básico: Entendiendo la Necesidad de una Implementación Mejorada
Implementar <
THE END
More about IA para la Detección de Anomalías en la Ciberseguridad de la Cadena de Suministro
- ¿Cómo elegir los juguetes adecuados para tu perro?
- Mejores peines para pulgas para perros de pelo largo
- ¿Qué hacer si su perro muestra síntomas de ansiedad?
- Cómo mantener los dientes de su perro limpios de forma natural
- Cómo entrenar a tu perro para dormir en su jaula
- Los beneficios de los rompecabezas para perros para la estimulación mental
- ¿Cómo construir confianza con un perro de rescate?
- ¿Cómo elegir la mejor correa para un perro de raza grande?
- Cómo prevenir quemaduras solares en la nariz y las orejas de tu perro
- ¿Cómo manejar a un perro con golpe de calor?
- Sistemas robóticos para kitting y ensamblaje en la cadena de suministro
- Automatización Robótica de Procesos (RPA) en la Cadena de Suministro Impulsada por IA